
Where can I get study material for the Cisco 400-251 exam,2020?If you use a trusted 400-251 dumps to prepare for the Cisco 400-251 exam, passing the Cisco 400-251 exam in one go is not difficult. Pass4itsure brings the best study guide, which is authentic, updated, verified, and available in PDF format.https://www.pass4itsure.com/400-251.html (Q&As: 665).Share the latest 400-251 practice questions, 400-251 exam videos……
400-251 CCIE Security
The 400-251 CCIE Security written exam validates experts who have the knowledge and skills to architect, engineer, implement, troubleshoot, and support the full suite of Cisco security technologies and solutions using the latest industry best practices to secure systems and environments against modern security risks, threats, vulnerabilities, and requirements.
Cisco 400-051 Study Guides, 50% Discount Cisco 400-051 Practise Questions Covers All Key Points
The 400-251 CCIE Security written exam has been retired as of February 24, 2020.
2020 New CCIE Security
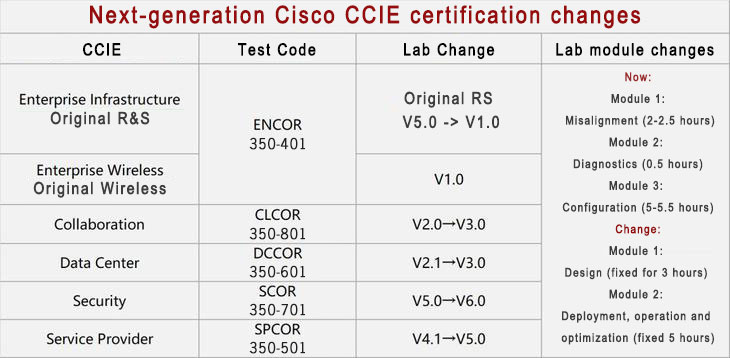
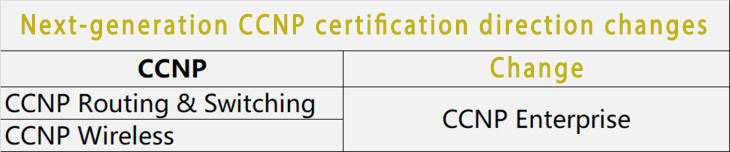
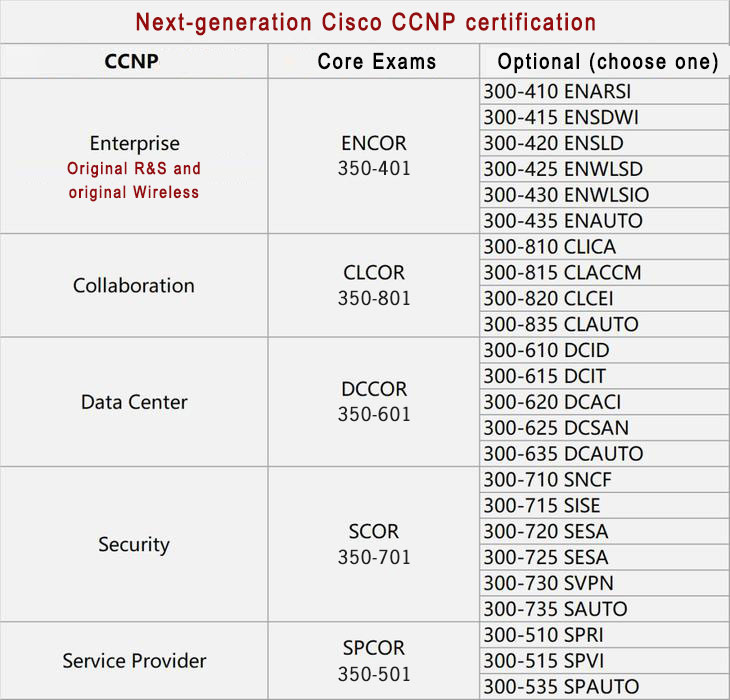
RS exit stake in history stage, RS direction changed to Enterprise direction, existing RS certification automatically upgraded to enterprise infrastructure certification after the release of new certification.
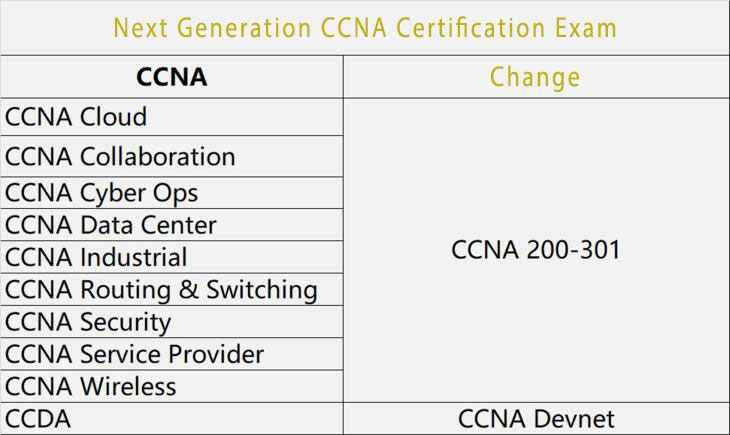
Design direction changed to DevNet direction, CCDA to DevNet Associate, CCDP to DevNet Professional.
The next generation CCIE is still valid for 3 years, but more than 3 years only need to choose to re-test the written test to activate, no need to test LAB activation.
400-251 CCIE Security – 350-701 CCIE Security
350-701 SCOR https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/scor-350-701.html
400-251 CCIE Security https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/400-251-ccie-security.html
| 400-251 CCIE Security written exam | February 24, 2020 |
| 350-701 CCIE Security exam | After February 24, 2020 |
| Pass4itsure 400-251 dumps | https://www.pass4itsure.com/400-251.html |
| Pass4itsure 350-701 dumps | https://www.pass4itsure.com/350-701.html |
Cisco Certification of other changes
Latest 400-251 practice questions(1-13)
Which port is used by ISE pxGrid services for inter-node communication?
A. UDP port 161 and 162
B. TCP port 443
C. TCP port 5222
D. UDP port 9995
Correct Answer: C

cause is the most probable?
A. Peer information is incorrectly configured on the remote IPsec router
B. The phase 1 policies are not compatible
C. The phase 2 policies are not compatible
D. Crypto ACLs are not correctly mirrored on both ends of the tunnel
E. Peer information is incorrectly configured on both sides of the tunnel.
Correct Answer: C
Which attribute cannot be used in Mobile Device Management (MDM) Authorization policy?
A. DaysSinceLastCheckin
B. DeviceRegistrationStatus
C. MDMServername
D. MDMServerReachable
E. NetworkAccess:EAPChaningResult
Correct Answer: E
Which statement a bout the wireless security tech nologies is true?\\’
A. WPA2-PSK mode provides better security by having same passphrase across the network
B. WPA2 provides message integrity using AES
C. WPA2-PSK mode does not allow a passphras? to be stored lo~cally on the device
D. WPA2 is more secure than WPA because it uses TKIP for encryption
E. WEP is more secure than WPA2 because it uses AES for encryption
F. WPA2-ENT mode does not require RADIUS for authentication
Correct Answer: B
Which three statements about the keying methods used by MACSec are true?(Choose three)
A. SAP is not supported on swicht SVLs.
B. SAP is supported on SPAN destination ports
C. MKA is implemented as an EAPlL packet exchange
D. Key management for host-to-switch and switch-to-switch MACSec sessions is provided by MKA
E. SAP is enabled by default for Cisco TrustSec in manual configuration mode.
F. A valid mode for SAP is NULL
Correct Answer: ACF
Which three loT attack areas as defined by OWASP are true? (Choose three)
A. Ecosystem access control
B. Local device vector injection
C. Remote data storage tempering
D. Local data storage
E. Middleware exploitation
F. Device physical interfaces
G. Vendor frontend API enumeration
Correct Answer: ADF
Which statement about zone-based policy firewall implementation is true?
A. A zone pair can have a zone as both source and destination
B. All the interfaces of the device cannot be the part of the same zone
C. An interface can be member of multiple zones
D. By default, traffic between the interfaces in the same zone is dropped
E. If an interface belongs to a zone, then the traffic to and from that interface is always allowed
F. If default zone is enabled, then traffic from zone interface to non-zone interface is dropped
Correct Answer: A

able to associate with the NTP server R1. What could be the possible cause?
A. R2 has incorrect NTP server address
B. R1 has incorrect NTP source interface defined
C. R2 has incorrect trusted key binded with the NTP server
D. R2 does not support NTP authentication
E. R2 should not have two trusted keys for the NTP authentication
F. R2 has connectivity issue with the NTP server
Correct Answer: C
Refer to the exhibit. One of the Windows machines in your network is experiencing a Dot1x authentication failure.
Windows machines are setup to acquire an IP address from the DHCP server configured on the switch, which is
supposed to hand over IP addresses from the 50.1.1.0/24 network, and forward AAA requests to the radius server at 161.1.7.14. Knowing that interface Gi0/2 on the switch may receive authentication requests from other devices and
looking at the provided switch configuration, what could be the possible cause of this failure?
aaa new model aaa authentication login default group radius aaa authentication login NO_AUTH none aaa
authentication login vty local aaa authentication dot1x default group radius aaa accounting dot1x default start-stop group
radius ! username cisco privilege 15 password 0 cisco dot1x system-auth-control ! interface GigabitEthernet0/2
switchport mode access ip access-group Pre-Auth in authentication host-mode multi-auth authentication port-control
auto dot1x pae authenticator ! vlan 50 interface Vlan50 ip address 50.1.1.1 255.255.255.0 ! ip dhcp excluded-address
50.1.1.1 ip dhcp pool pc-pool network 50.1.1.0 255.255.255.0 default-router 50.1.1.1 ! ip access-list extended Pre-Auth
permit udp any eq bootpc any eq bootps deny ip any any ! radius server ccie address ipv4 161.1.7.14 auth-port 1645
acct-port 1646 key cisco ! line con 0 login authentication NO_AUTH line vty 0 4 login authentication vty
A. aaa login authentication is not configured
B. authentication port-control is not set on interface gi0/2
C. an incorrect dhcp pool is configured
D. aaa dot1x authentication is not configured
E. Open authentication is not enabled on interface gi0/2
F. an incorrect radius server address is defined
G. an incorrect pre-authentication acl is configured
Correct Answer: E
Your customer wants to implement Cisco Firepower IPS and the requirement to start off with secure policy. However, a
monitoring period of 2 weeks is applied to ensure that the policy is evaluated against real traffic without causing an
outage before going in to full blocking mode. You decide to (???) of the default policies as a base and set the policy
action to ensure that false positives are not dropped. Which two policies to achieve these requirements are true?
A. Set IPs policy to trust
B. Set IPs policy to Monitor
C. Base the IPS policy on the default Advanced Security over Connectivity policy
D. Base the IPS policy on the default Balanced Security and Connectivity policy
E. Base the IPS policy on the default Connectivity over Security policy
F. Base the IPS policy on the default Security over Connectivity policy
G. Set IPS Policy to No Drop
Correct Answer: BD
Refer to the exhibit. R2 is getting time synchronized from NTP server Rl.It has been reported that clock on R2 cannot
associate with the NTP server R1. Which possible cause is true?
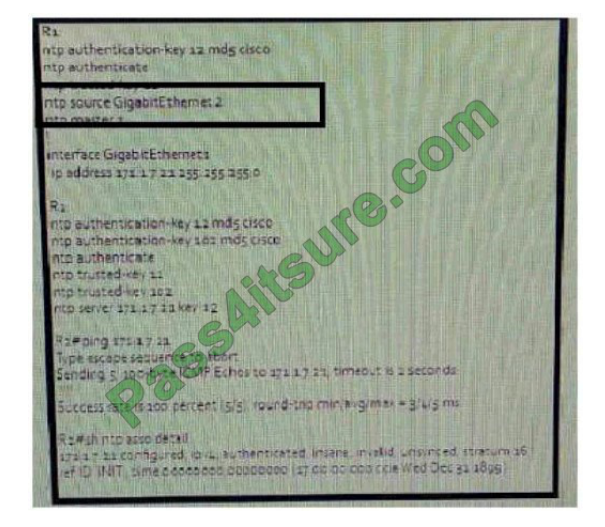
B. R1 has an incorrect NTP source Interface defined
C. R2 should not have two trusted keys for the NTP authentication
D. R2 does not support NTP authentication
E. R2 has an incorrect trusted key binded with the NTP server
F. R2 has incorrect NTP server address
Correct Answer: B
Which statement correctly describes AES encryption algorithm?
A. It does not use substitution and permutation principle
B. It uses three encryption keys of length 128, 192 and 256
C. Reapplying same encryption key three times makes it less vulnerable then 3DES
D. Theoretically 3DES is more secure then AES
E. It provides only data integrity
F. It uses the block of 64 bits
Correct Answer: B
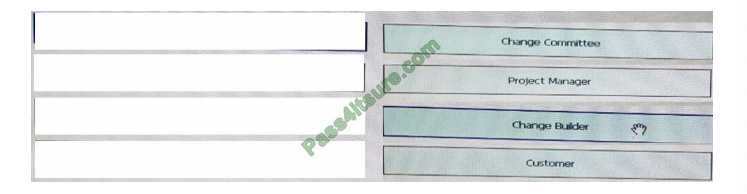
Drag and drop the role on the left onto their responsibility in the change-management process on the right.
Select and Place:

Cisco 400-251 pdf dumps download from Google Drive
[PDF] Free 400-251 pdf dumps https://drive.google.com/open?id=1KqNSnbpwYWH01EqLJGLuHNuNuv0Ekrno
Pass4itsure discount code 2020
Latest IT exams brain dumps that cover the complete actual test questions .Pass your exam in the first attempt with reliable Pass4sure training materials.

Summarize:
Buy the exam dumps to pass Cisco 400-251 exam in one try.https://www.pass4itsure.com/400-251.html Latest 400-251 dumps!