Everyone knows that the Cisco 300-915 practice test will undoubtedly help you pass the 300-915 exam. So, here are the latest Cisco 300-915 practice questions and answers to help you! Of course, if it is not enough, please click https://www.pass4itsure.com/300-915.html Perfect 300-915 pdf dumps – 300-915 exam dumps.
Key words
Cisco 300-915 Exam Dumps | Cisco 300-915 PDF Dumps | Cisco 300-915 PDF Questions| Cisco 300-915 BrainDumps | Cisco 300-915 Practice Test | Cisco 300-915 Practice Questions
Cisco 300-915 Exam Dumps: With Free 300-915 Pdf Download
The Cisco 300-915 exam pdf dumps questions with verified answers :
| Drive.google | Update (2020) |
| Cisco 300-915 exam pdf dumps | https://drive.google.com/open?id=1ft8P3WOyn3t3STdVugoJz9mxN_lSRmaZ |
Verified Cisco 300-915 Dumps of Pass4itsure
If you are hesitant in deciding on the Cisco 300-915 exam preparation materials, then you should try our recommendation for the Cisco 300-915 exam dump. There, you may get a 300-915 pdf dumps Perfect. You will also get answers to 300-915 dumps pdf questions, and 100% pass guarantee. You can save all your money and time with Pass4itsure practice materials because they are determined to provide the best Cisco 300-915 dumps on the market.
The latest and best Cisco 300-915 practice questions
(300-915 DEVIOT)
Certifications: Cisco Certified DevNet Professional, Cisco Certified DevNet Specialist – IoT
Duration: 90 minutes
Available languages: English
Valid Cisco 300-915 Practice Questions: pass4itsure
QUESTION 1
Which command is used to package a Docker-style Cisco IOx app using ioxclient?
A. ioxclient docker create helloworld:1.0.
B. ioxclient docker-app helloworld:1.0.
C. ioxclient docker package helloworld:1.0.
D. ioxclient docker helloworld:1.0.
Correct Answer: C
QUESTION 2
As part of an IoT project, an organization is developing an edge application that will run on a gateway to securely
transmit sensor information it receives into an IoT cloud. Based on the Agile software development lifecycle, the
development team is planning to implement a CI/CD pipeline.
Which two methods should be suggested to make the software development lifecycle more secure during the
implementation and testing? (Choose two.)
A. Perform automated code reviews prior to deployment.
B. Implement auto-provisioning security inspection for the code.
C. Perform on-going penetration testing on the system.
D. Perform a GAP analysis on current security activities and policies.
E. Train members of the team in a secure software development lifecycle methodology such as OWASP.
Correct Answer: DE
QUESTION 3
An IoT application has been built into the application CI/CD pipeline. The application needs credentials to access other
applications, APIs, and cloud resources.
When should the credentials be inserted into the application using the CI/CD process?
A. hard coded into your application code base
B. during application runtime
C. after application testing
D. during application build time
Correct Answer: A
QUESTION 4
Which two actions must be completed before starting the process of sending IoT data to the cloud via edge routers?
(Choose two.)
A. Measure the voltage, power rating, and quiescent current for the sensors that send data to the cloud.
B. Gather the hardware (MAC) addresses of local and cloud routers to ensure low latency communication.
C. Collect information about the CPU architecture in the cloud and edge to ensure that they match.
D. Gather the interval, the volume, and the latency that the data must be provisioned with.
E. Collect information about growth, required elasticity, and high availability of the provisioning process.
Correct Answer: DE
QUESTION 5
When constructing a Python script for data extraction using GMM APIs on a Cisco Kinetic Cloud platform, how should
the API authentication be implemented?
A. Generate the API keys once and edit the permissions as needed.
B. Generate and use the API keys for the required access level from the Kinetic Cloud application.
C. Use a complex username and password with 128-bit encryption.
D. Use a complex username with an auto-generated password from the Kinetic Cloud application.
Correct Answer: B
QUESTION 6
Which connector is southbound?
A. horizontal connector
B. cloud connector
C. device connector
D. universal connector
Correct Answer: C
QUESTION 7
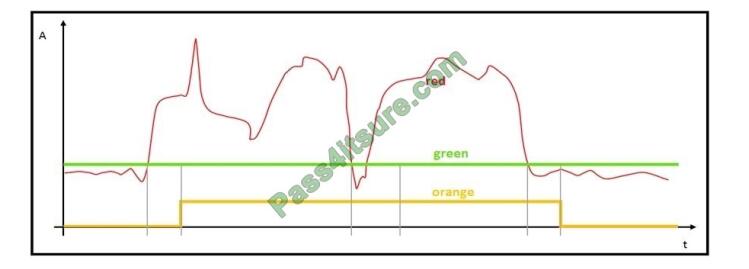
Refer to the exhibit. The red line represents the energy consumption of an industrial machine.
Which two statements about the graphs are true? (Choose two.)
A. The orange graph is expected to drop to zero for a brief period around the midpoint on the x axis.
B. The red graph contains the raw data points.
C. The green graph is the mean value of the data points.
D. The green graph does not give us any valuable information.
E. The orange graph has three values on the y-axis.
Correct Answer: BC
QUESTION 8
Which two security approaches help build a strong authentication scheme? (Choose two.)
A. connection based on location
B. session IDs accepted only from cookies
C. maximum allowed connections
D. user logout
E. session logout because of inactivity
Correct Answer: CE
QUESTION 9
A company is collecting data from several thousand machines globally. Which software component in the overall
architecture is the next destination of the dataflow after the data has been gathered and normalized on the edge data software?
A. relational database: MySQL
B. historian database: influxDB
C. message broker: Apache Kafka
D. dashboard: Node.js web app
Correct Answer: B
QUESTION 10
An IoT engineer is responsible for security at an organization. Humans and machines need to be allowed to access
services like database or compute on AWS. The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
A. Create a central secret system for humans and machine to obtain very short-lived dynamic secrets to access any
service.
B. Humans cannot be trusted, and each time they authenticate they should be issued with dynamic secrets. Machines
can be trusted, and they can be issued with static credentials.
C. Maintain a different service associated to secret systems to issue access.
D. After a user is authenticated by any trusted system, the user can be trusted to use any service.
Correct Answer: A
QUESTION 11

Refer to the exhibit. Based on the MQTT client output, which action should be taken so that the connection to the broker
can be established?
A. Change the username/password.
B. Open port 1883 on the network firewall.
C. Change the IP address of the broker.
D. Add the certificate.
Correct Answer: A
QUESTION 12
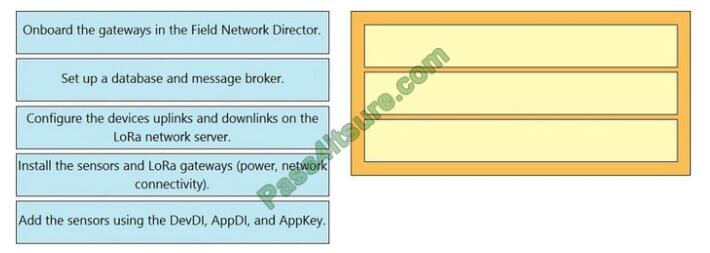
DRAG DROP
The network team of a large international airport is creating a sensor network on their site using the Cisco LoRaWAN
solution. Drag and drop the actions from the left to right needed to implement this project. Not all options are used.
Select and Place:
Correct Answer: 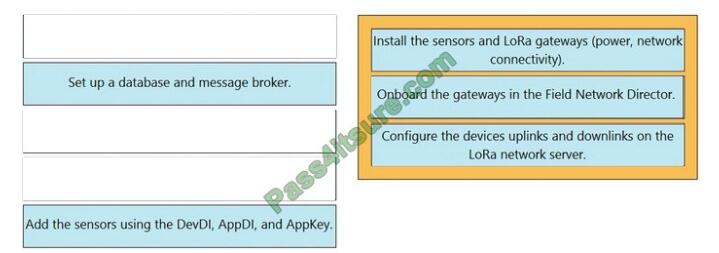
Reference: https://www.cisco.com/c/en_in/solutions/internet-of-things/lorawan-solution.html#~stickynav=3
Pass4itsure discount code 2020

[Download Free Cisco 300-915 Dumps https://drive.google.com/open?id=1ft8P3WOyn3t3STdVugoJz9mxN_lSRmaZ]
Summarize:
The above provides free Cisco 300-915 practice questions, Cisco 300-915 dump pdf, you need to use them multiple times in order to ensure your success in the actual exam. https://www.pass4itsure.com/300-915.html Cisco 300-915 exam questions. This is the right way to go, so you can pass the exam perfectly.